Base is quickly becoming a serious option for production-grade Web3 applications. As your organization evaluates or scales on Base, one of the most consequential—but often misunderstood—decisions you face is how to access the network reliably and cost-effectively: through Base RPC nodes.
RPC (Remote Procedure Call) nodes serve as gateways between your applications and the Base blockchain. The quality of that gateway affects user experience, uptime, security, and your overall cost profile. So this guide will help you:
- Understand what Base RPC nodes do in business terms.
- Compare self-hosted Base nodes vs. managed RPC providers, with clear trade-offs.
- Evaluate providers and architectures using criteria aligned to risk, cost, and growth.
- Apply a practical decision framework and scenario-based “playbook” for your organization.
- See where a provider like RPC Fast can fit into your infrastructure strategy.
If your teams are already working with Base—or you’re planning a rollout in 2026—this guide provides the context and questions you need to make informed choices.
The 2026 Base ecosystem: Official reference points
As Base matures into a primary execution layer, CTOs must anchor their strategy in the network’s canonical resources before evaluating third-party enhancements. In 2026, a robust infrastructure audit starts with three official pillars:
- The Base Node provider directory: The first stop for vetting any provider. Base maintains a curated list of partners categorized by archetype—from performance-first dedicated nodes to privacy-preserving gateways.
- The canonical node repository: For teams considering self-hosting or hybrid fallbacks, the official base/node repository is the source of truth for Docker builds, client support (Reth, Geth, Nethermind), and production hardware specs.
Basics of utilizing Base for your project
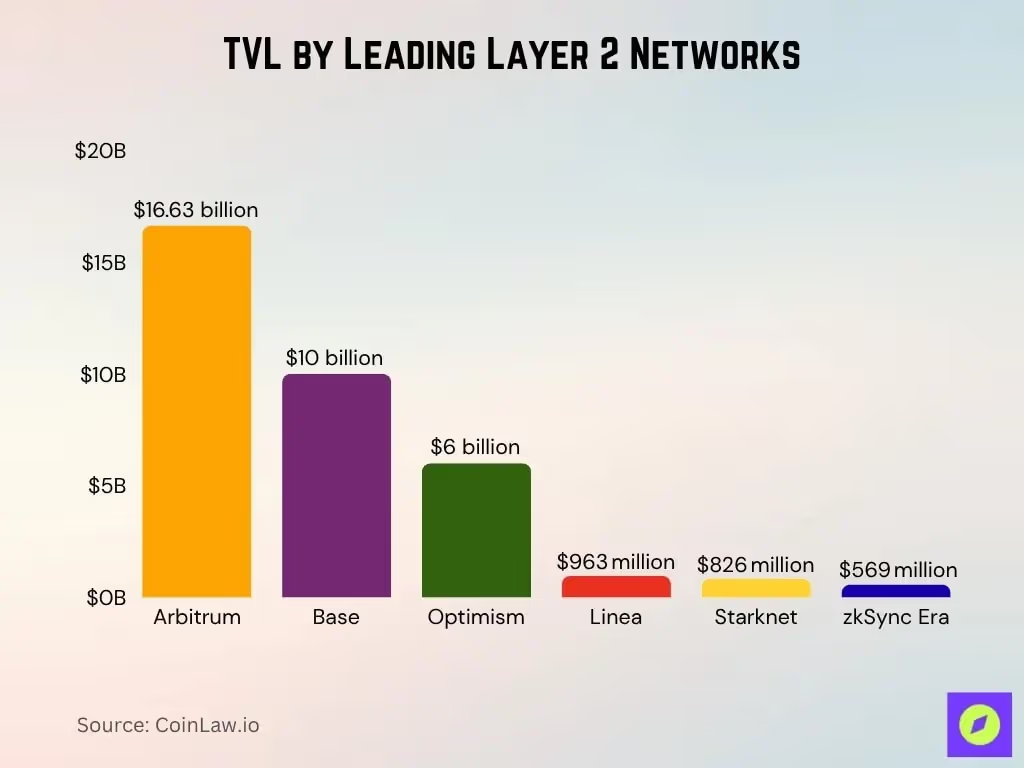
Base is a Layer 2 (L2) blockchain built on the OP Stack, designed to provide cheaper, faster transactions while inheriting security from Ethereum. For many projects, Base offers:
- Lower transaction costs compared to mainnet Ethereum.
- Higher throughput and better user experience for consumer-facing products.
- Integration with the broader Ethereum ecosystem, tooling, and liquidity.
In 2026, several trends continue to make Base especially relevant:
- Maturing L2 ecosystem: L2s are no longer experimental; they are hosting production DeFi, consumer apps, and enterprise use cases.
- User expectations: End-users expect near-instant interactions with apps, not “wait for your transaction to confirm” workflows.
- Cost pressure: Teams are under pressure to reduce gas costs while maintaining security and reliability.
- Multi-chain strategies: Organizations are moving from “Ethereum only” to multi-chain—Base, other L2s, and sidechains.
➣ Base can unlock new product and business models, but only if your access to Base is reliable, performant, and secure. That access is mediated through RPC nodes.
The role of RPC nodes
To interact with Base—reading data, submitting transactions, querying smart contracts—your application typically uses an RPC endpoint.
An RPC node is a server (or cluster of servers) that:
- Stores and syncs data from the Base blockchain.
- Exposes a standardized API (the RPC interface).
- Responds to your app’s requests: “What’s the latest block?”, “What’s this wallet’s balance?”, “Send this transaction.”
From a business perspective, an RPC node is the front door to the network. If the “door” is slow, unstable, or misconfigured, your users feel it immediately.
Why RPC quality differs and matters
Here are some cases demonstrating how RPC nodes' quality directly impacts your project:
UX:
- Slow RPC responses mean laggy interfaces and delayed confirmations.
- Errors or timeouts translate into failed actions and support tickets.
Revenue and conversion:
- In DeFi or trading, latency and reliability affect execution quality and user trust.
- In consumer apps, slow or failing interactions increase churn.
Operational risk:
- Outages at the RPC layer can take your product “offline,” even if Base itself is fine.
- Misconfigured nodes can introduce security and compliance risks.
Cost profile:
- Over-provisioning infrastructure or using misaligned pricing models can lead to significant overspend.
- Under-provisioning leads to throttling and degraded performance.
➣Treat RPC nodes as mission-critical infrastructure, on par with your core backend, databases, and payment rails—not as “just another API.”
Architecture choices: Self-hosted vs. Managed vs. Hybrid RPC
As your teams propose architectures for Base, you will typically see two primary options:
- Self-hosted Base nodes (run by your team on your cloud or accessed on-prem)
- Managed RPC providers (external providers that run Base nodes and expose RPC endpoints to you)
Each option has advantages and trade-offs. And there’s always a third way—a hybrid and multi-provider approach.
Self-hosted Base nodes
Your team deploys, configures, and maintains one or more Base nodes, often in your existing cloud infrastructure. Your engineers handle everything from hardware sizing to node upgrades. Alternatively, you can hire a Base engineer, like one from Dysnix, and they’ll handle everything securely in the closed perimeter for your project.

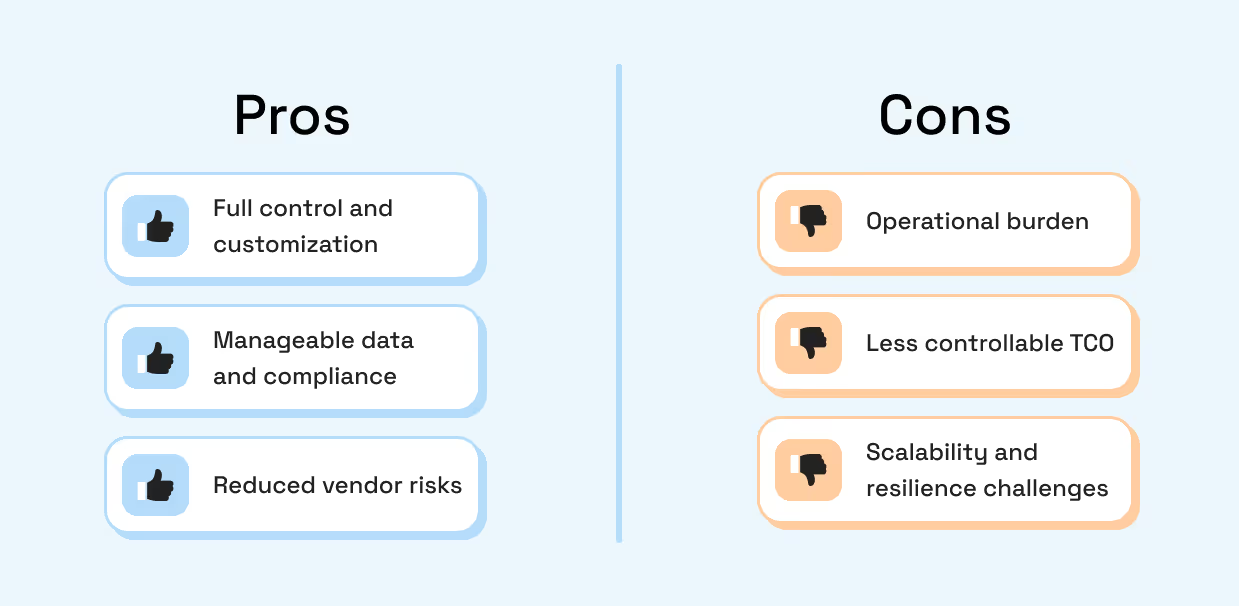
Pros
- Control and customization:
- Full control over configuration, security posture, and performance tuning.
- Ability to integrate deeply with internal systems and governance processes.
- Data and compliance:
- Potentially easier to align with specific data residency or compliance requirements if you control the environment.
- Vendor risk:
- Reduced reliance on a single external RPC provider; you own the stack.
Cons
- Operational burden:
- Requires specialized expertise in blockchain node operations, which can be scarce and expensive.
- 24/7 monitoring, upgrades, incident response, and capacity planning are your responsibility.
- Hidden total cost of ownership (TCO):
- Infrastructure costs (compute, storage, bandwidth) plus the cost of engineers and support.
- The “soft costs” of outages, slow incident resolution, and ongoing maintenance are often underestimated.
- Scalability and resilience challenges:
- Building a globally distributed, highly available, low-latency RPC layer is non-trivial.
- You’ll need redundancy, load balancing, and failover strategies.
➣For most organizations, self-hosting is only justified when there are strong requirements for control, compliance, or customization, and when the organization has (or is willing to build) the relevant operational capability.
Managed RPC providers
You consume Base RPC as a service. Providers like RPC Fast run the infrastructure, and you access it via secure endpoints, typically with SLAs, dashboards, and support.
Pros
- Reduced operational overhead:
- Your teams don’t need to become Base node experts.
- Upgrades, scaling, and incident response are handled by the provider.
- Faster time to market:
- You can get reliable Base access in hours or days instead of weeks or months.
- Built-in scalability and resilience:
- Good providers offer multi-region setups, load balancing, caching, and redundancy by default.
- You benefit from economies of scale and provider expertise.
- Predictable cost models:
- Usage-based or tiered pricing that can be mapped to business metrics (e.g., requests, transactions, active users).
Cons
- Vendor risk and dependency:
- Outages or incidents at the provider can impact your product.
- Switching costs, although often manageable, are not zero.
- Less granular control:
- You may not control every detail of configuration or upgrades.
- Some custom use cases may require additional negotiation or workarounds.
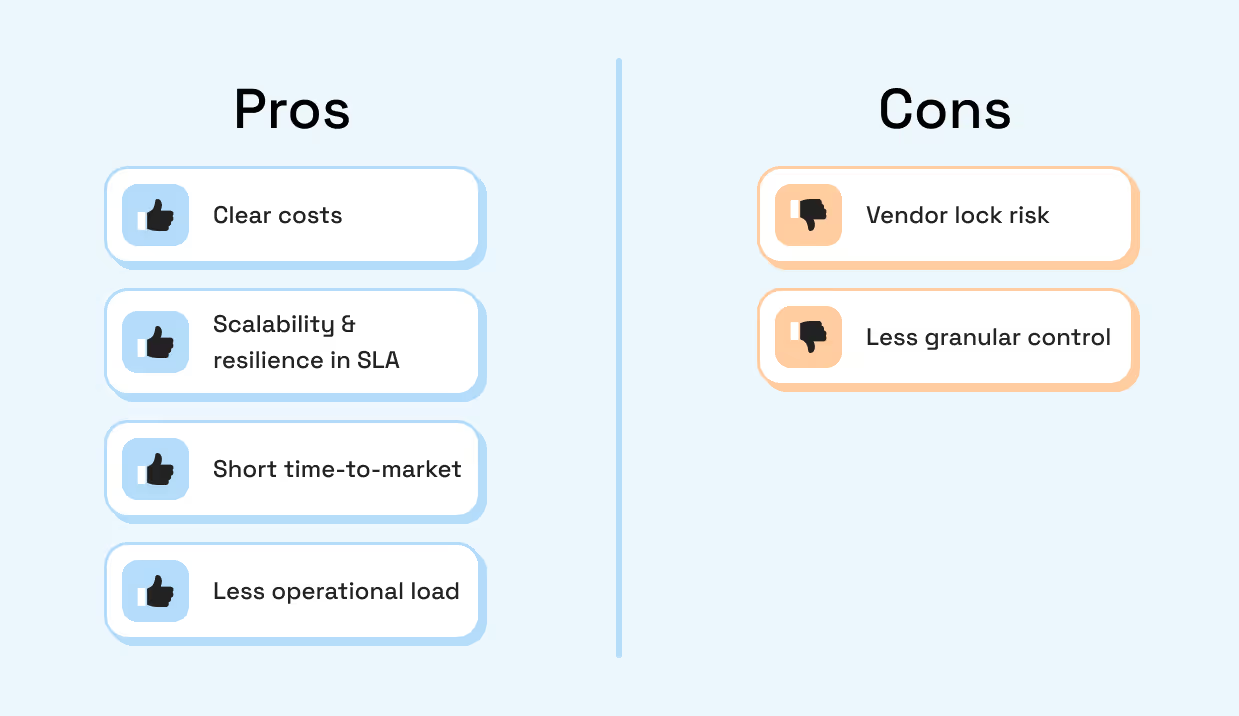
➣For many teams—especially startups and scaling teams—managed RPC is the default choice. The key is to select a provider and architecture that fit your risk appetite, growth plans, and compliance needs.
Hybrid and multi-provider approaches
Increasingly, mature teams adopt a hybrid model:
- Primary access via a managed provider.
- Secondary/backup access via a second provider or internally managed fallback nodes.
This approach can significantly reduce vendor risk while maintaining internal complexity at a manageable level.

➣Ask your team not just “self-hosted vs managed?” but “what combination of providers and internal capabilities gives us the best balance of control, resilience, and cost?”
Reference pattern: The HFT "fast-path" setup
For latency-sensitive operations, the hybrid model has evolved into a specific routing pattern:
- Fast-path (Dedicated RPC): All UX-critical reads (
eth_call,eth_getBalance) and transaction submissions are routed to private, region-locked endpoints. - Heavy-path (Specialized/Archive): Event indexing (
eth_getLogs) and historical state queries are offloaded to archive-specialized nodes to prevent head-of-line blocking on the trading path. - Hedged requests: For mission-critical reads, the system sends requests to two providers simultaneously, accepting the first valid response—a pattern that effectively "buys down" tail latency at the cost of higher request volume.
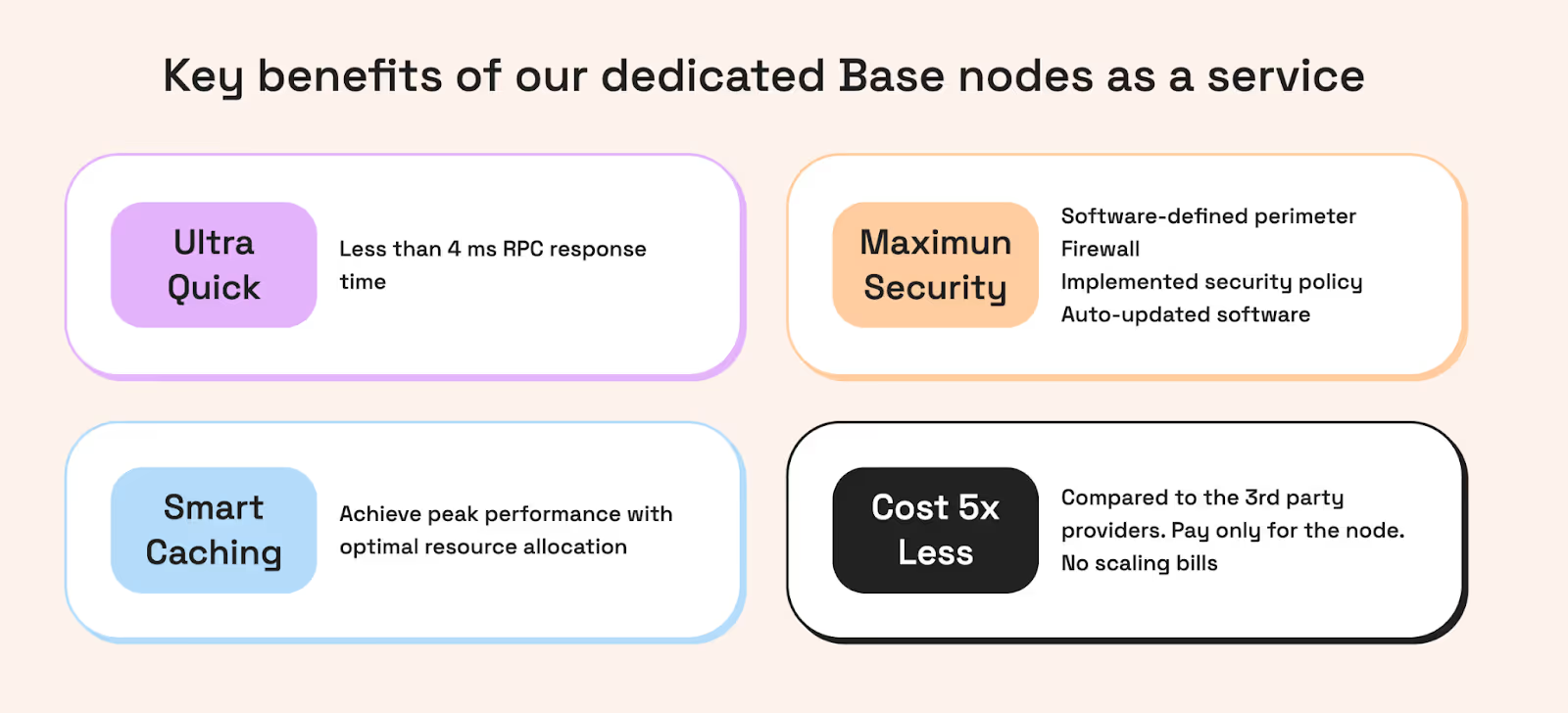
Key evaluation criteria for Base RPC in 2026
When your team evaluates Base RPC options—whether self-hosted or managed—they should be guided by criteria that directly map to business outcomes. Below are the core dimensions to explore, along with the best questions to ask your provider.
HFT requirements: Beyond "average" latency
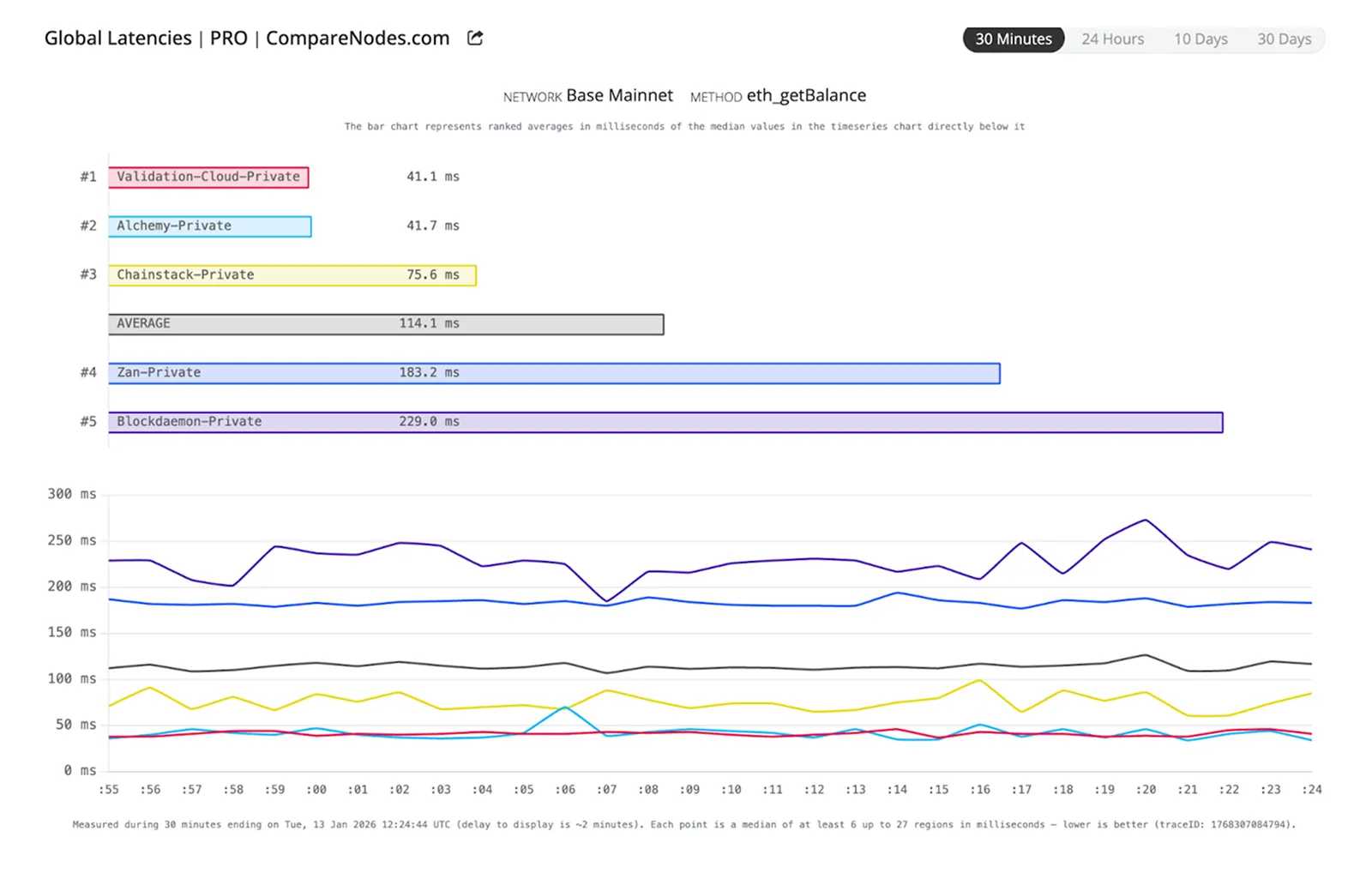
For latency-sensitive trading, liquidations, or arbitrage, "fast" is a baseline, not a differentiator. In 2026, CTOs evaluate performance through a more granular lens:
- Jitter and tail latency: Average response time is a vanity metric. HFT-grade RPC requires stability in the p99 and p99.9 percentiles. Jitter—the variance between your fastest and slowest responses—is often more disruptive to trading bots than a slightly higher, but stable, latency.
- Consistency and staleness: In a fast-moving L2 environment, "node lag" is a silent killer. Your evaluation must include how a provider detects and mitigates stale reads, ensuring your bots aren't executing trades based on a state that is even one block behind.
- Write-path propagation: Read-path speed (quotes) must be paired with write-path efficiency (transaction submission). Evaluate how the RPC layer handles
eth_sendRawTransactionduring mempool spikes—does it queue, drop, or multi-stream to the sequencer?
Reliability and availability
Uptime:
- Describe your standard architecture for high availability on Base.
- What is the historical uptime of the service?
- Are there contractual SLAs, and what do they include (credits, notifications, incident response)?
Redundancy and failover:
- Are there multiple nodes, regions, or data centers?
- How is failover handled—automatically, or does your team need to manually redirect traffic?
Security
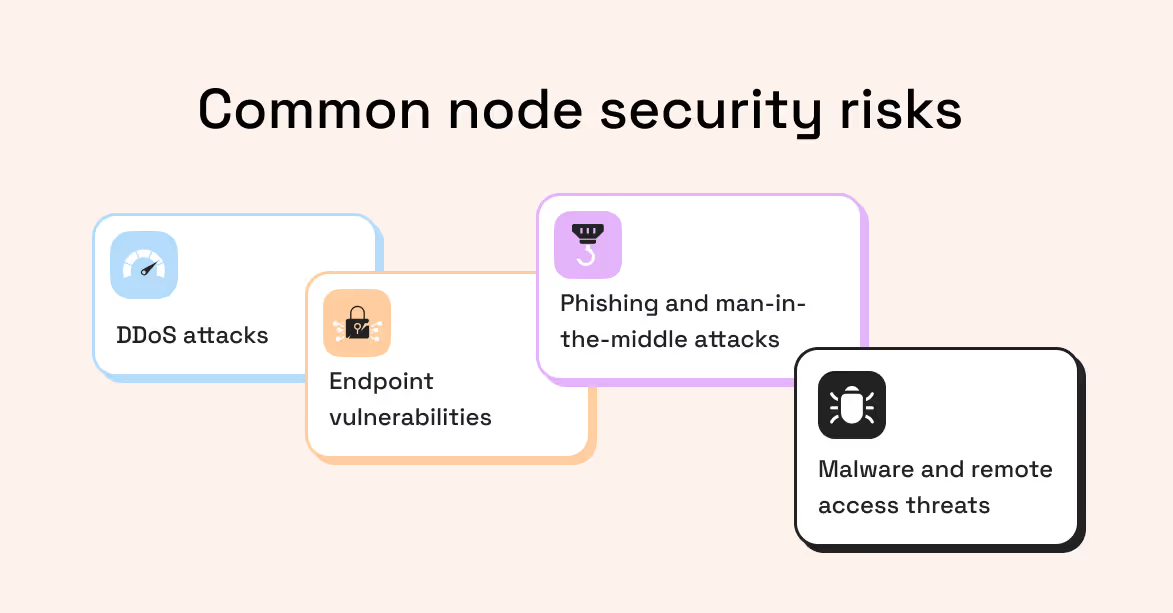
Access control:
- How are your API keys and access tokens secured?
- Are there IP allowlists, rate limits, and authentication controls in place?
DDoS and abuse protection:
- How does the provider protect your endpoints from volumetric attacks or abuse that could degrade service?
Data integrity and privacy:
- How are logs and sensitive data handled?
- Are there clear policies around retention and access?
Observability
Monitoring and dashboards:
- Can you see request rates, latency, error codes, and other key metrics?
- Is there an interface for your teams to troubleshoot issues quickly?
Alerting and notifications:
- Can you set alerts based on thresholds?
- How does the provider communicate incidents (status page, email, webhooks, etc.)?
Support and SLAs
Support tiers and response times:
- Is support email-only, or do you get chat or phone support?
- What are the response and resolution time targets for different severity levels?
Escalation paths:
- In a critical incident, how quickly can you talk to someone who can actually fix the issue?
- Walk us through a recent critical incident and how you handled it.
Pricing and cost control
You have to get a clear answer for “How would our expected traffic profile translate into monthly costs?” and “What safeguards exist against unexpected cost spikes?” questions to protect your budget on the very first stage of cooperation.
Pricing model:
- Is it per-request, per throughput tier, or flat-rate?
- How are spikes handled—throttling, overage fees, or both?
Budget predictability:
- Can you estimate costs based on your traffic projections?
- Are there alerts or caps to prevent runaway bills?
Compliance and governance (where relevant)
- Data residency:
- Can you choose specific regions or data centers?
- Auditability:
- Can you get logs and evidence for compliance audits if needed?
➣Do not treat RPC as a black box. Demand the same level of clarity, metrics, and SLAs that you would from a critical SaaS or cloud infrastructure provider.
Top Base RPC providers to consider in 2026
Many infrastructure players support Base, but for most organizations, the short list typically includes a mix of:
- A specialized RPC provider focused on performance and observability (e.g., RPC Fast).
- One or more large multichain platforms (Alchemy, Infura, QuickNode, Ankr) that already sit in your stack for other networks.
For a C-level audience, the goal is not to memorize feature matrices but to understand the positioning of the main options and how they differ in risk, cost, and capabilities. Below is a high-level view of five widely used providers that support Base RPC in 2026:
- RPC Fast—performance-focused RPC provider with an emphasis on latency, reliability, and monitoring for production workloads.
- Alchemy—full-stack Web3 platform with Base support and extensive “enhanced APIs” and tooling across chains.
- Infura—long-standing infrastructure provider from Consensys with strong Ethereum lineage and multichain support.
- QuickNode—performance- and analytics-focused provider, positioning itself as one of the fastest RPC options globally, including EVM chains.
- Ankr—Web3 infrastructure platform offering both public and premium RPC, with broad multichain coverage including EVM L1s and L2s.
These providers are all capable of supporting production use cases on Base; the key question is which one (or combination) best matches your performance, compliance, and cost priorities.
Building your 2026 Base provider shortlist: A CTO’s decision flow
According to the Base’s archetype logic, here’s how your 2026 procurement should focus on matching provider types to specific workload profiles.
For HFT and production-grade DeFi, follow this selection logic:
1. Identify your archetype mix
Don't shop for a "vendor"; shop for an architecture. Most mature stacks now combine:
- The performance core: A dedicated RPC provider (like RPC Fast) focused on private endpoints, regional affinity, and SRE-grade observability.
- The resilience layer: An independent secondary provider or a self-hosted fallback using the base/node stack to mitigate vendor-specific outages.
- The tooling lane: A specialized gateway for heavy tracing, debugging, or archive queries, keeping these resource-intensive calls off your trading fast-path.
2. Apply "must-pass" procurement gates
- The latency gate: Require p95/p99 metrics for your specific method mix in your target regions.
- The observability gate: Insist on per-method error taxonomy and the ability to export metrics to your internal monitoring (Datadog/Prometheus).
- The cost-predictability gate: 2026 pricing has shifted toward complex "Compute Units" (CU) or "Request Units" (RU). Require providers to translate your expected burst patterns into a transparent monthly cost model.
3. Execute a "stress-test" pilot
Move beyond the happy-path demo. A today’s pilot should simulate:
- Partial degradation: How does your system react when the provider is "up" but latency spikes by 200ms?
- Burst handling: Replay a high-volatility trading window to see where rate-limiting or 429 errors trigger.
- Failover recovery: Measure the exact time it takes for your router to switch from primary to secondary endpoints during a simulated regional outage.
High-level feature matrix: Base RPC providers at a glance
Disclaimer: This is an opinionated and high-level overview, not a precise feature audit. We emphasize that the offer is subject to change at any time, so please contact the providers for more details.
Legend:
- ✅ —strong/primary focus
- ~ —available/partial/less of a strategic focus
TL;DR
- If you prioritize deep observability, predictable performance, and a focus on secured and flash-speed RPC, a specialist like RPC Fast can be a compelling option.
- If you want a single pane of glass across many chains plus advanced APIs (NFT, token, webhooks), platforms like Alchemy, Infura, QuickNode, and Ankr are strong options.
- Many mature teams run a multi-provider strategy (e.g., RPC Fast + one large multichain provider) to de‑risk outages and gain flexibility.
Where RPC Fast fits in
A provider like RPC Fast is designed to take the operational complexity of running Base RPC nodes off your plate, while providing the performance, reliability, and observability your teams need.
In a typical setup with a provider like RPC Fast:
- Your applications connect to high-performance Base RPC endpoints, often with global routing and smart load balancing.
- You gain access to dashboards and metrics that show request volumes, latency, and error rates, helping your teams quickly spot and resolve issues.
- You benefit from expertise and economies of scale—the provider’s entire business is optimized for blockchain RPC, which is challenging to replicate in-house.
You can still:
- Add internal nodes for specific use cases (e.g., analytics, compliance) if needed.
- Use more than one provider for redundancy in mission-critical scenarios.
- Adjust your architecture over time as your Base usage grows.
➣The key is to think of providers like RPC Fast as infrastructure partners, not just vendors: part of your broader strategy for delivering secure, reliable, and efficient access to Base.
Practical decision framework for C-level leaders
To mix the mentioned criteria and a list of providers into an actionable and productive process, you can guide your teams through a structured decision framework.

Step 1: Define requirements
Work with your product, engineering, and security leads to clarify:
- Expected request volume and growth over the next 12–24 months.
- Target latency in key user regions.
- Acceptable downtime windows and RTO/RPO expectations.
- Compliance and data residency requirements, if any.
- Target budget range for Base infrastructure, including RPC.
Questions to ask your team:
- “Under what conditions would an RPC outage or slowdown be catastrophic for our business?”
- “What are our minimum acceptable thresholds for latency and uptime on Base?”
Step 2: Choose a core strategy
Based on your requirements and risk appetite, decide whether you are:
- Strategy A: Primarily using a managed provider, with internal or secondary providers as backup (often the most efficient for startups and growth-stage companies).
- Strategy B: Primarily self-hosting, with managed providers as overflow or backup (fits the teams with strict compliance or control requirements).
- Strategy C: Multi-provider managed, with no self-hosting (when you want strong resilience without building deep node operations expertise).
Step 3: Evaluate providers against a checklist
For each potential managed provider, review:
Ask for concrete data where possible: metrics, status pages, references, or case studies.
Step 4: Run a pilot
Before committing fully:
- Start with a pilot where a portion of your traffic (or a new product) runs on the target setup.
- Measure latency, error rates, and stability under realistic load.
- Test incident response by simulating failures (e.g., region outages, traffic spikes).
Use the pilot results to:
- Validate that the provider and architecture meet your expectations.
- Refine your traffic routing strategy (e.g., multi-region, failover rules).
- Adjust usage tiers or configurations to optimize cost.
Step 5: Plan for scale and evolution
Your Base usage is likely to evolve. Work with your teams and providers to:
- Establish scaling thresholds (when to upgrade tiers, add more regions, or add a second provider).
- Align on upgrade and maintenance plans (how node software updates are handled).
- Revisit your architecture quarterly or semi-annually as traffic and the Base ecosystem grow.
➣Treat RPC decisions as an ongoing process, not a one-time procurement. Build in reviews and pilots to keep your infrastructure aligned with your business trajectory.
Turning Base RPC into a strategic advantage
The value you derive from Base depends heavily on one foundational piece: how your applications talk to the network via RPC nodes. To maximize this value, you do need to:
- Recognize that RPC is a core part of your infrastructure, not an implementation detail.
- Ensure your teams evaluate self-hosted vs. managed vs. hybrid approaches with clear eyes.
- Demand robust performance, reliability, security, observability, and cost control from any RPC solution.
- Use a structured decision framework and scenario-based thinking to align architecture with business goals.
- Engage with providers like RPC Fast as strategic partners to reduce operational risk and accelerate your roadmap.
Your role is to set the direction: insist that Base RPC be treated with the same rigor and strategic intent as any other critical infrastructure decision. The rest—implementation details, configuration, and tuning—can and should be owned by the right technical leaders and partners.
If you want to go deeper, the next step is to have your team:
- Map this guide’s criteria to your current or planned Base deployments.
- Identify gaps in your current RPC setup.
- Prepare a recommendation—potentially including providers like RPC Fast—aligned with the framework outlined here.

.avif)

















.svg)
.svg)
.svg)

