Sniper bots share one goal: enter first at a sane price while avoiding traps. But every missed fill and extra 30–50 ms on Solana costs P&L. So, good bots optimize the full path from signal to confirmation, tune priority fees by slot conditions, validate liquidity and authorities, and exit fast on anomalies. Bad ones spam, ignore mempool reality, skip safety checks, and leak edge through retries.
Teams use snipers to solve three problems:
- Win scarce fills during new listings;
- Reduce slippage under burst TPS;
- Avoid rugs on permissionless pairs.
The bar is sub-100 ms submit, consistent first-10 confirmations in target slots, and a measurable drop in revert rate and loss events. This article explains the basics and advanced advice for teams looking to adapt a specific sniper bot for Solana.
Also, instead of a name dump, we group community-endorsed sniper bots by what drives outcomes: latency path, priority fee logic, strategy control, and safety checks. Use this to match your stack to your risk, speed, and ops constraints.
Solana sniper bots in 2026: what’s different from 2025
Solana’s fee markets, MEV infrastructure, and bot competition have evolved. Priority fees and bundle routes are more standardized, typical retail bots are faster, and professional desks treat sniper infra as part of a broader HFT stack instead of a toy side‑project.
In this update, we keep the core playbook but add 2026‑level considerations: tighter latency SLOs, bundle‑aware routing, more mature risk controls, and ops practices for teams that run multiple snipers across chains.
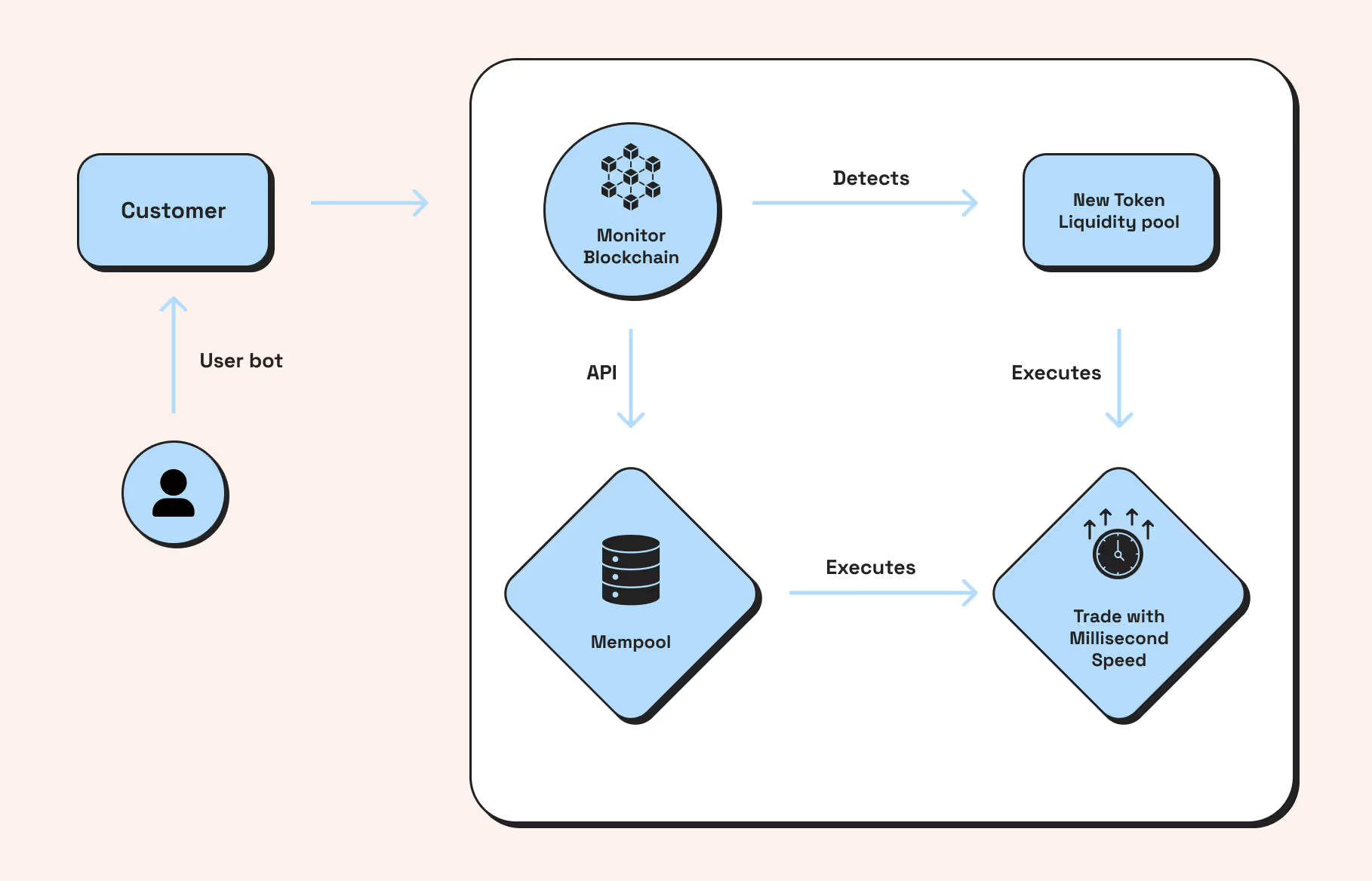
What is a Solana sniper bot?
A Solana sniper bot is an automated trader that monitors new token listings and on-chain signals, then submits a buy transaction in the first viable slots to capture early price movement while constraining slippage and risk. The core loop is simple but unforgiving: detect, price-check, route with priority fees, confirm early, and exit on anomaly.
An anomaly is any signal that increases loss odds or invalidates the entry thesis. Examples:
- Liquidity mismatch: sudden drop in on-chain pool depth, disabled swaps, or concentrated spoof liquidity on the target DEX pool;
- Authority risks: mutable mint authority, freeze authority present, recent ownership transfer, or blacklisted program IDs;
- Trading path issues: priority fee spikes without leader proximity, repeated preflight reverts, or rising duplicate/nonce errors;
- Price integrity: rapid >5–10 percent deviation from oracle/VWAP within a few slots, or asymmetric slippage vs. contemporaneous trades;
- Contract behavior: transfer taxes, trading pausable flags, blocked sell functions, or delayed mint updates detected during simulation;
- Network conditions: slot congestion with rising blockhash-not-found, leader schedule change increasing confirmation lag, or RPC rate limiting on submit/confirm;
- Post-fill health: abnormal MEV patterns around the fill, widening spreads with no replenishing depth, or failure to place an immediate exit order.
On Solana, slot timing, local fee markets, and RPC path latency define the edge; poorly tuned bots spam or confirm late, which increases reverts and worsens fill prices. Well-engineered bots add pre-trade liquidity and authority checks, dynamic fee curves by slot congestion, and post-trade watchdogs to avoid rugs on permissionless pairs.
For an overview of Solana transaction flow, fee markets, and priority fees that sniper strategies depend on, see the official Solana docs.
Who needs sniper bots?
Teams that live or die by first fills use sniping bots: quant traders chasing early momentum on new listings, market makers securing inventory before spreads widen, and retail-to-pro desks automating entries during micro-spikes.
They want three outcomes: consistent first-10 confirmations in target slots, lower realized slippage during burst TPS, and fewer loss events from rugs or disabled sells.
From the infrastructure point of view (our favorite one 😉), these teams have lots in common:
- Priority-aware RPC and leader proximity: Low-variance, close-to-leader RPC with reliable QUIC, websockets, and priority fee passthrough. Multi-endpoint failover with health checks.

- Deterministic fee strategy and pre-simulation: Dynamic priority fee curves tied to recent block congestion, with preflight simulateTransaction against the same endpoint used for submit.
- Reliable event ingestion for listings and pools: WebSocket subscriptions on DEX program events and token registry/indexers with backfill on disconnects.
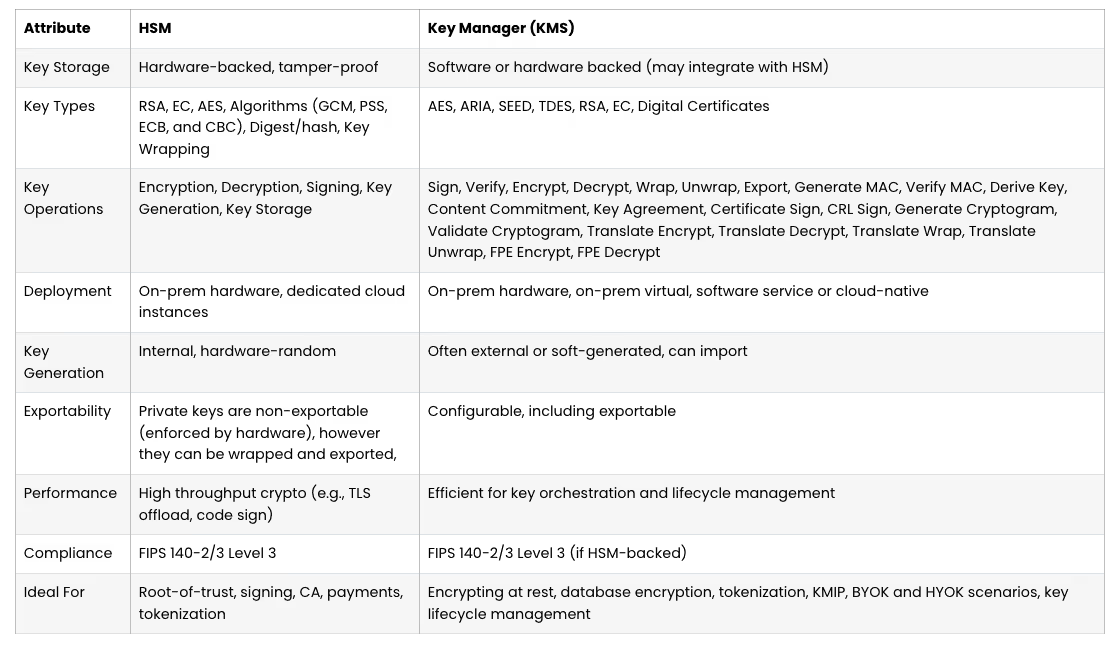
- Key management and secure deployment: HSM or KMS-backed keys, short-lived session keys, per-strategy key segregation, and rate-limited signers.
- Liquidity and authority safety checks: Pre-trade checks for pool depth, mint freeze authority, mutable mint authority, and program allowlists.
- Slot timing and leader awareness: Use the leader schedule to time submissions and adjust fee curves when the next leaders are known.
- Robust submit pipeline with retries and dedup: Idempotent transaction builders, durable nonces or recent blockhash refresh, exponential backoff, and duplicate signature detection.
- Observability and post-trade watchdogs: Metrics for P50/P95 submit latency, confirmation rank, revert rate, realized slippage, and anomaly exits. Structured logs with slot and leader attribution.
- Competitive routing and MEV awareness: Program-aware routing across DEX paths and JIT liquidity behavior.
If you rely on Solana for launch-day liquidity, arbitrage, or short-hold momentum, a sniper bot is an execution necessity, not a nice-to-have.
What qualities should a good sniper bot have?
Beyond speed, a good sniper bot must be predictable, governable, and cheap to operate at scale. You want SLOs for latency and success rate, circuit breakers that pause strategies on anomaly thresholds, and a permissions model that separates research code from production keys.
Budget control matters: fee caps per strategy, per-slot spend guards, and daily risk limits tied to expected value keep P&L intact during hype days.
Auditability is essential for compliance and post-mortems: immutable logs with slot, leader, fee, and route attribution, plus reproducible simulations for every trade.
Operability decides uptime: blue‑green deploys, feature flags, and rollbacks within minutes, backed by 24/7 paging on confirmation lag, revert spikes, and RPC health.
Vendor resilience: multi-RPC routing, regional failover, and clear exit plans from third-party libraries reduce single points of failure when the chain is hot.
Scalability comes from idempotent transaction builders, exponential backoff retries, and segregated key management in secure VPCs to handle 1,000-plus snipes per day without leaks or spam penalties, all deployed on Kubernetes for zero-downtime rolls and autoscaling during spikes.
Solana sniper bot platforms (2026 technical comparison)
Here is a table of some Solana bot platforms, focusing on key differentiators for technical buyers.
*Fees are indicative and can change quickly. Always confirm current fee schedules and any rebates/points inside each bot or on its official docs before relying on them.
TL;DR
- If you want a single, heavy‑duty Solana terminal:
Go with Axiom Trade—it’s the most “all‑in‑one” option (snipes, perps, yield, analytics) if you’re fine living in a web app. - If you want the highest‑end Telegram experience:
Pick Trojan on Solana—very fast, feature‑dense, and designed for serious on‑chain memecoin trading from your phone. - If you prefer a lightweight web terminal first:
Use Photon Sol—simple, clean, and fast as a browser‑based front end; many traders pair it with a Telegram bot. - If you care about “smart money” and automation in one place:
Choose GMGN.ai—best fit if you want new‑token feeds, copy trading, and Anti‑MEV in the same workflow. - If you’re trading across multiple chains as well as Solana:
BullX NEO and Banana Gun Bot both give you multi‑chain reach with strong Solana support. - If you want the simplest Solana starter bot with serious infra behind it:
BONKbot is still the go‑to “just tap and trade” Telegram flow for many users.
Solana sniper bot fees and costs
Most platforms charge a percentage per transaction, typically ranging from 0.5 percent to 1 percent. Some offer a lower base fee but add a fixed cost per transaction for priority routing via Jito validators. And ~0.006 SOL per transaction can accumulate rapidly on high-volume days.
In practice, base fees are tiny, but priority fees dominate. A single snipe transaction can range from a fraction of a cent to several cents worth of SOL, depending on congestion and your CU price.
Beyond platform fees, consider the implicit costs of a sniping bot:
- Priority fees: Your bot’s dynamic fee strategy determines how much SOL you spend to outbid others for block inclusion. Poorly tuned fees waste capital or lead to missed fills.
- RPC costs: Dedicated or premium RPC endpoints, essential for low latency, come with a subscription cost. This is a fixed overhead for speed.
- Failed transactions: Each revert still consumes network fees. A high revert rate from flawed logic or poor RPC adds up.
Evaluate the total cost of ownership, not just the headline percentage. A cheaper bot with higher revert rates or slower fills can be more expensive in lost opportunity and wasted fees.
Best practices for Solana sniper bot users (in the form of a playbook)
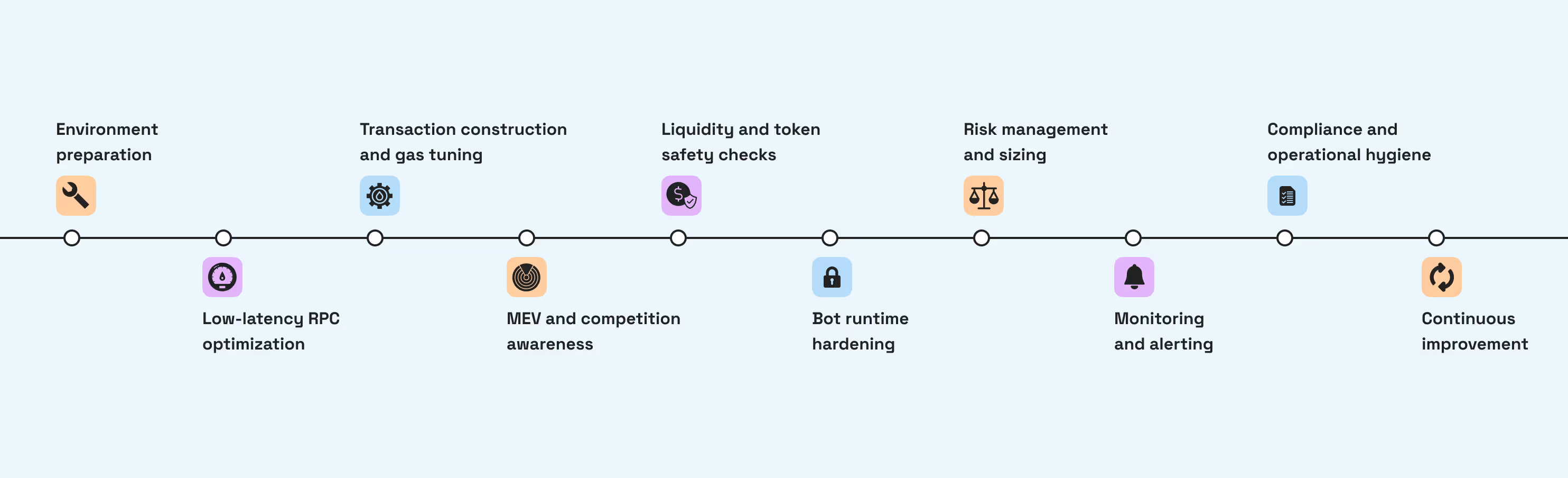
Prepare your environment
- Use a dedicated wallet per bot/strategy; fund only what you can afford to lose.
- Separate hot wallets from long-term vaults; rotate private keys periodically.
- Prefer hardware wallets for treasury; keep sniping keys in secure, minimal-permission hot wallets.
- Lock down your endpoint: IP whitelisting, HTTPS only, and avoid sharing RPC URLs publicly.
Optimize your RPC for low-latency
- Choose the geographically closest RPC regions to your host/server.
- Use a high-performance plan with guaranteed concurrent connections and prioritized mempool access.
- Enable/benchmark:
- Preflight disabled for speed when you understand the risk (
skipPreflight=true). commitment: "processed"for earliest fills; fall back to"confirmed"for larger size.- WebSocket subscriptions for
logsSubscribeandprogramSubscribeto react to events instantly.
- Preflight disabled for speed when you understand the risk (
- Monitor key RPC metrics: p50/p95 latency, rate-limit events, dropped WebSocket subscriptions, and slot lag.
- Keep automatic backoff and multi-endpoint failover (primary + backup RPCs) to avoid stalls.
Transaction construction and gas tuning
- Tip the leader (priority fees) based on live congestion; implement dynamic fee scaling.
- Keep transactions minimal: single instruction paths; avoid unnecessary compute budget bloat.
- Use
computeUnitLimitandcomputeUnitPricewisely; pre-calculate typical CU cost per strategy. - Batch building: pre-sign templates where possible; only mutate volatile fields at runtime.
- Retry policy: short exponential backoff, unique recent blockhash per attempt, and immediate abandon on slot rollover.
MEV and competition awareness
- Understand Solana’s leader schedule: pre-fetch who’s producing next blocks; adjust timing/fees.
- Avoid predictable patterns: randomize small timing offsets, vary tip ladders.
- Detect sandwich or backrun surfaces in your strategy and minimize leakiness (don’t broadcast too early).
- Use private or low-broadcast paths where supported by your RPC or partner relays to reduce copy-trading.
Bundle‑aware and private routing for Solana snipers in 2026
In 2026, the biggest edge difference between hobby snipers and professional desks is how they route transactions:
- Public RPC vs private relays—when to use public mempool vs private routes to reduce copy‑trading and sandwich exposure.
- Bundles and pre‑confirmation flows—how bundles affect first‑confirmation rank and what constraints they impose on latency and fee curves.
- Tip strategies for bundle vs non‑bundle routes—different fee ladders and risk limits.
- Failover between routes—design patterns to fall back from advanced routes to standard RPC when conditions worsen.
Liquidity and token safety checks
- Validate mint, decimals, and freeze authority; check for mint revocation patterns and upgradeable programs.
- Inspect AMM pools: real liquidity depth, LP token age, and owner permissions.
- Simulate swaps locally before sending; compare expected vs simulated output.
- Maintain denylists and heuristics for:
- Honeypots (sell-blocking)
- High owner tax/transfer hooks
- Suspicious metadata changes or program upgrades
Bot runtime hardening
- Run on dedicated, low-jitter servers (preferably same region as RPC). Keep CPU pinned and clocks synced (NTP).
- Persist state safely: recent blockhashes, seen signatures, and last-seen pool states.
- Add watchdogs: restart on stale slot, WS disconnect, or repeated
BlockhashNotFound. - Implement structured logging with per-trade UUIDs; ship logs to a central sink for post-mortems.
Risk management and sizing
- Set max slippage per venue and per token risk tier.
- Cap per-trade and per-block exposure; throttle on volatility spikes.
- Use circuit breakers:
- Halt on 3 consecutive failed sims
- Halt on price deviation > X% from the oracle/anchor price
- Halt on RPC error rate > threshold or slot lag > threshold
- Daily P&L limits and kill-switch bound to a secure channel (e.g., signed command or authenticated webhook).
Governance, audit, and compliance in 2026
- Map sniper strategies to internal risk policies (which strategies are allowed on which venues, tokens, and sizes).
- Enforce change management: approvals for strategy logic changes, fee curve updates, and new venues.
- Maintain immutable audit logs of strategies, code versions, configs, and transaction traces for each trade.
- Add formal sign‑off for production keys and mandatory reviews after large P&L swings or near‑miss incidents.
Monitoring and alerting
- Dashboards: RPC latency, tip spend, fill rate, revert reasons, CU consumption, and P&L by strategy.
- Alerts: WS disconnect, rate-limit, unusual tip spend, slippage breach, oracle divergence.
- Record full transaction lifecycle: built → simulated → sent → landed → settled with timestamps.
Compliance and operational hygiene
- Respect rate limits; implement jitter and queueing.
- Log dependencies and versions (Solana core, SDKs, AMM adapters) for reproducibility.
- Keep up with Solana runtime and token program changes; re-verify assumptions after upgrades.
- Secure secrets via KMS or vault; never store keys in code or plain env files.
Continuous improvement
- Run A/B tests on fee ladders, timing offsets, and route selection.
- Maintain a sandbox with a mainnet fork or low-size live testing before scaling position sizes.
- Post-incident reviews with concrete action items; prune features that add latency without edge.
Best Solana sniper bots in 2026
How to pick fast:
- Need speed without validators: Maestro, Photon, Sol Trading Bot Pro
- Compete on microseconds and fees: Jupiter + priority, Helius x Jito, Birdeye + custom submitter
- Win on logic and tests: Triton SDK, TensorSwap SDK, Anchor templates
- Losses from rugs, not misses: Rugcheck + Maestro, Birdeye Gates, SolSniffer
- Run a desk and want spread: Phoenix MM Sniper, OpenBook MM Sniper, Tensor NFT Sniper + MM
Benchmarks to demand before funding
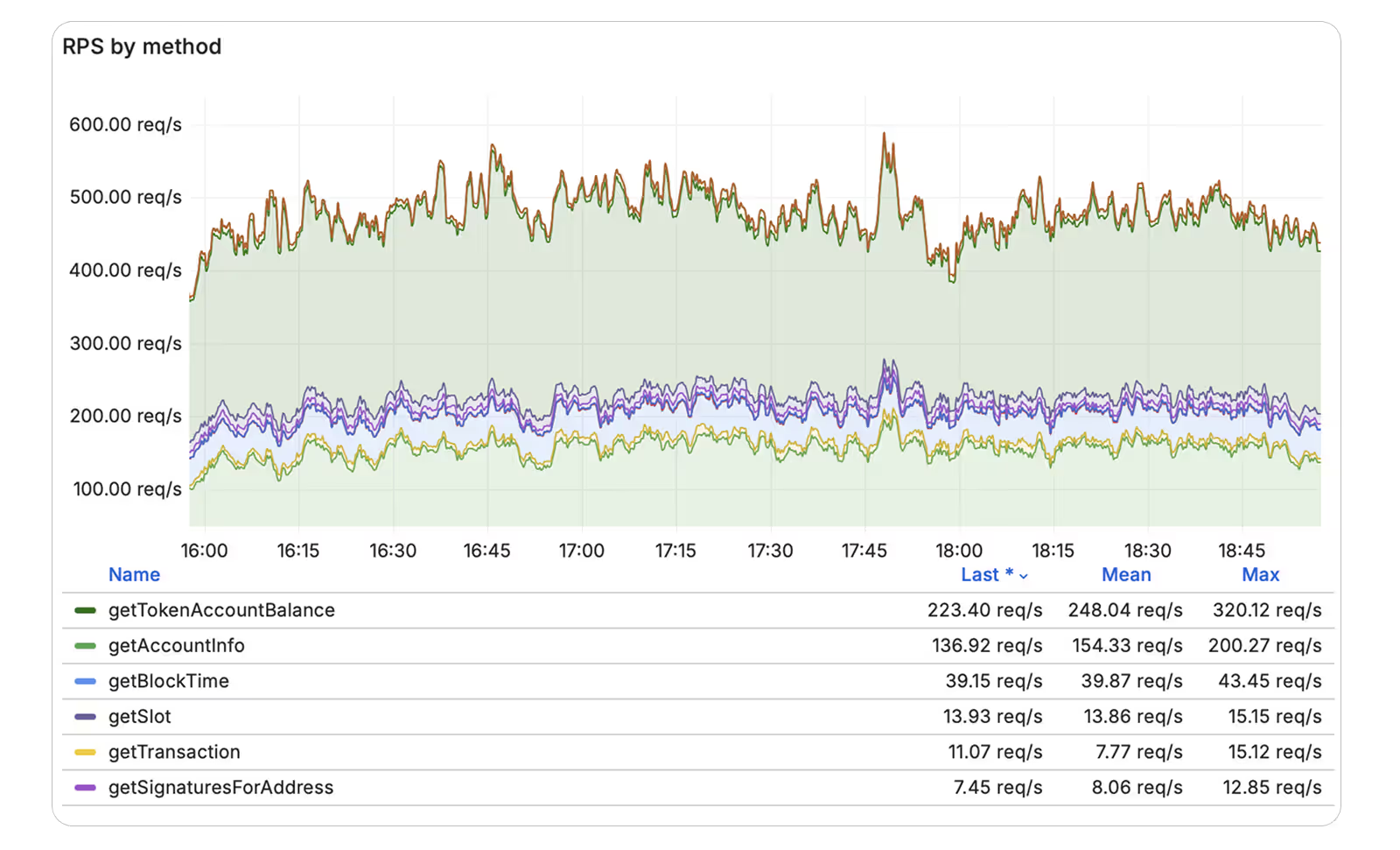
- Repro script: 100 simulated token launches over 7 days
- Measure: P50/P95 submission, confirmation rank, failure rate, realized slippage, exit-on-anomaly time
- Include: RPC endpoints, slot leader proximity, fee settings, machine type, region
- Share: monthly latency and P&L review with owned post-mortems
Get your sniper bot plan ready
The bots that win pair sub-100 ms submission, slot-aware priority fees, and pre-trade safety checks. Group your options by what you need most: speed without validators, bundle/priority control for first-confirmation rank, strategy frameworks for custom logic, or safety-first filters to avoid loss events during token launches.
Your selection should come with proof. Ask vendors for a 7-day repro covering 100 events with identical RPC and fee settings. Review P50/P95 submit, confirmation rank, revert rate, realized slippage, and time-to-exit on anomaly. Require ops basics: multi-RPC failover, clear backoff, per-strategy keys, and alerts on confirmation lag. If your team lacks low-latency depth, use a managed service with SLOs and monthly latency/P&L reviews.
Next step. Map your execution path and fees before you swap bots. RPC Fast will help benchmark your current route, tune priority fees by slot conditions, and recommend a bundle-ready setup tailored to your trading strategies, market trends, and risk limits.

.avif)


















.svg)
.svg)
.svg)

